And its time for another networking club meeting. To start, I will remind everybody of the networking club rules:
- If you are the last one to leave, remember to hide a raisin underneath the welcome mat.
Easy enough. Ok, let’s get started. Last time we met, we were talking about how networking has a bunch of different layers involved, and how computers on the same network can send packets to each other.
The lesson today is all about IP routing. As in, what a router does. You know why they call it a router? Because it routes things, you dingus. Duh.
In the previous article, I explained how two computers on the same network talk to each other. What we will cover today is how computers can talk to each other when they are on different networks.
IP Networks
Computers and IP addresses are grouped into networks. For example, your home network may be 192.168.1.0. Then computers on it may be 192.168.1.1, 192.168.1.2, 192.168.1.3 and so on.
If you have any pattern recognition skills whatsoever, you should notice something here. All of the computers on this network have an IP address that starts with the same thing. Only the last digit is different.
Now, somebody else’s home network, maybe lil’ Timmy down the street, maybe that network is 192.168.255.0, with computers 192.168.255.1, 192.168.255.2, 192.168.255.3, and so on. That is a different IP network. You can tell, because… it is a different IP network. Different IP networks have different addresses, in the same way different houses have different addresses.
Basically, every physical location – a home, a business, and so on – each of them have their own IP network, and their own router. And they manage their own little chunk of the world.
But it would be pretty useful if your computer could talk to Timmy’s computer, right? Or, better yet, if your computer can talk to a computer on google’s network. You know, so you can use it to search or whatever kids do these days.
So we want computers to communicate across networks. If only we could somehow connect all these tiny little networks into one big network…
As it turns out that has already been done, and it is called the internet. You may have heard of it. The internet is this big magic thing that lets computers on all these tiny little networks talk to computers on other tiny little networks.
In order to understand how that works, we first need to understand exactly how computer networks are defined. And in order to understand that, we need to understand what IP addresses actually are.
IP Addresses
I got a secret. I don’t trust you at all, seeing as how you are a random stranger, but I will tell you anyway, because it will blow your mind.
IP addresses are not four decimal numbers.
GAAAAAAAAASP!
Yes, it is true, you have been lied to this entire time. IP addresses, as it turns out, are actually binary. Oh, the horror.
But, if you know anything about computers, that actually makes sense, because… computers work in binary. So… yeah.
IP addresses are, more specifically, 32 bits. A bit is just a 0 or a 1. If we take the IP address 192.168.1.5 and convert it to binary, we get this:
11000000 10101000 00000001 00000101
Each group of 8 bits is called a byte, and when we are talking about networking they are specifically called octets, because, you know, there are 8 bits. And again, networking people need different terms for everything.
So IP addresses are actually just 32 bits, or 4 octets. Now, the thing to keep in mind is that binary is just a different way to represent numbers. It isn’t as if binary numbers have different values, they are just represented differently. For example, if we count to 10, here are the decimal = binary comparisons:
1 = 1, 2 = 10, 3 = 11, 4 = 100, 5 = 101, 6 = 110, 7 = 111, 8 = 1000, 9 = 1001, 10 = 1010
So every binary number has an equivalent decimal representation, and vice versa. But we as humans, given we have ten of these finger thingies, decided that decimal was the bee’s knees. At the end of the day, though, it all does the same thing. So don’t be scared.
You may have also noticed that each of the four numbers in an IP address ranges from 0 to 255. Now you can see why. If you have 8 bits, the lowest number you can represent is 0 (00000000), and the highest number is 255 (11111111).
There is one other thing about binary we need to learn: bitwise AND. Bitwise AND is like an arithmetic operation – you got your adds, subtracts, and so on – the basic stuff. Binary numbers have all those as well, but they also have an additional operation, bitwise AND.
To perform a bitwise AND with two binary numbers, simply line them up on top of each other – just like when you add normal numbers. Like this:
11011010 00001110
00111001 11101010
Then, right below them, we will write the answer. In each column, write a 1 if both of the numbers above it are 1. Otherwise, write a 0. This gives us the answer:
00011000 00001010
This is why it is called bitwise AND. If the bit from the first number is 1 AND the bit from the second number is 1, then the resulting bit is 1. Otherwise, it is a 0.
Why are you showing me all of this binary nonsense?
Understanding the binary nature of IP addresses is actually crucial in order to understand how routing works. Fortunately for you, you have already learned everything you need to learn about binary – let’s get back to the networking.
Subnet Masks
When you run the command ipconfig on windows, you will see something like this:
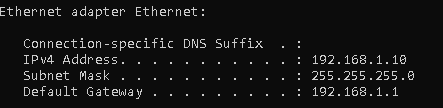
The IPv4 address is your IP address, of course. But you will notice there is another line there called subnet mask. It almost looks like an IP address, right?
It kind of is. And also… kind of isn’t. But it isn’t a coincidence that it looks like an IP address, because the subnet mask and IP address are basically partners. Not romantically, mind you, purely platonic. But neither of them would be very useful without the other.
IP addresses are actually made of two parts: The network portion and the host portion. Network here means roughly what you would expect – it is a grouping of computers that are all connected, like all the computers in a house or business. Host in this context refers to an individual device on the network like a computer or phone.
Why is it called the host portion, and not the computer portion? I don’t know, but the networking folks are fancy and decided they wanted to use fancy words, to suit their fancy. Boom, fancyception. So deal with it.
Suppose the IP address of your computer was 192.168.1.117. What is the network portion, and what is the host portion? In this case, the network portion is probably the first three digits – 192.168.1 – and the host portion is the last digit, 117. The network portion tells the rest of the world how to get to you, like a zip code on a piece of mail. The host portion is how the router on your network knows it goes to your computer specifically and not something else on the network.
The network portion is always on the left side of the IP address and the host portion is always on the right. But their sizes actually vary – the network portion isn’t always the first three digits. How can you tell what size the network portion is? Well, that is exactly what the subnet mask is for.
Subnet masks, like IP addresses, are 32 bits. So if we have the subnet mask 255.255.255.0, the bits look like this:
11111111 11111111 11111111 00000000
Subnet masks help us find the network portion of an IP address. If you ever want to find out what the network address is for your computer’s IP address, you simply bitwise AND it with your subnet mask, like so:
11000000 10101000 00000001 00000101 (192.168.1.5)
11111111 11111111 11111111 00000000 (255.255.255.0)
=
11000000 10101000 00000001 00000000 (192.168.1.0)
Our computer is on the network 192.168.1.0. And when you think about it that makes sense – every computer on the network will be 192.168.1.X, so the subnet mask basically threw away that X and gave us just the network address shared by all hosts on our network.
So the subnet mask lets us know which bits are part of the network portion, and which bits are part of the host portion. And, when we use bitwise AND, we are left with only the network portion.
Note that because the subnet mask only shows us which bits are part of the network portion, and because the network portion is always on the left side of an IP address, the subnet mask always starts with 1s and ends with 0s. And they are always in groups – you never have a sequence like 0101, because the network and host portions don’t mix, they are just grouped together side by side.
One more thing – because we talk about IP addresses and their associated subnet masks so often, there is a handy notation for combining them called CIDR. For example, if my IP is 192.168.7.50 and my subnet mask is 255.255.255.0, then we could also write that as 192.168.7.50/24. 24, in this case, is the number of 1 bits in our subnet mask. If the subnet mask was instead 255.255.0.0, then it would be 192.168.7.50/16, because if you convert that subnet mask to binary you will find the first 16 bits from the left are all 1.
Get to the point already! Its freezing out here!
The point is, you got an IP, that IP belongs to a network, and the subnet mask helps you find what network that is. And the only reason any of that matters is when it comes to the routing table.
Routing Table
Every device on a network stores a routing table in memory. You can see it on windows with the command route print. Here is an example:
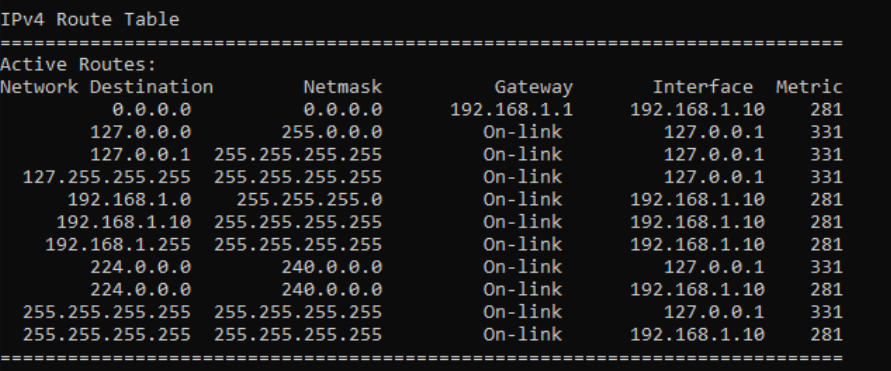
This is like the map in Dora the Explorer – it’s the one you need to know that gets packets where they need to go – it just doesn’t break out into song every time you use it.
When your computer sends an IP packet, it asks this question:
Where do I send this packet to?
And it consults the routing table to find the answer.
Imagine the year was 1990, and you wanted to call somebody. You knew their name, but not their phone number. In that case, you could look up their number in a phone book using their name, and proceed to call them.
The routing table is pretty similar. We look through the list of all possible destinations, and once we find the matching network we can get the associated gateway and interface we need to send the packet to.
Before we get to what those are, though, let’s think about the routing table a bit longer. How, exactly, do we pick the matching network on the left side?
First, we take the IP address we are going to send to, and bitwise AND it against every subnet mask (netmask) in the routing table. Remember that this finds what the network address would be. We then compare the result of that with the network destination field. If they match, then we know that route is a valid route to that destination.
What if there are multiple routes to a given destination? How do we decide between them? In that case, we choose the route that is the most specific – the one that has the subnet mask with the most 1’s. It is like if you were sending snail mail to your dear grandmother, who happened to live next door to you. If you bring it to the post office it will get to your grandma, but you could also walk next door and hand it to her. That second route is more specific – it wouldn’t work for anybody but your grandma.
And finally, if even after that step you still have multiple matching routes that “tie”, then you use the metric column. Metric represents which route has a higher priority and in windows a lower number is a higher priority. This mainly comes into play when you are connected to a network via multiple interfaces – wifi and wired, for example. In that case, the wired interface likely has a lower metric, because it is more desirable to use that than wifi.
Routing Table Example
That’s nice. Unfortunately I wasn’t listening that entire time, could you run it by me again?
Joke’s on you, I was going to do that anyway. And to make it easier for you, I will let you take a peak at the routing table again:

Suppose our IP is 192.168.1.7, and we are trying to send an IP packet to 192.168.1.8. What route is chosen?
If we bitwise AND the destination IP against 255.255.255.255, we get the exact same IP back – 192.168.1.8. But that doesn’t match the destination on the left, which is 255.255.255.255.
If we bitwise AND against 240.0.0.0, we get 192.0.0.0, which doesn’t match the left side, so we continue on.
If we bitwise AND against 255.255.255.255, we get 192.168.1.8 (which shouldn’t surprise you, because we did that already), and it doesn’t match 192.168.1.10 or 192.168.1.255.
If we bitwise AND against 255.255.255.0, we get 192.168.1.0, which matches the left side. We found a matching route.
If we bitwise AND the next two items, neither of the results equals 127.0.0.1 or 127.0.0.0. Then we conclude by doing bitwise AND against 0.0.0.0, which yields 0.0.0.0 and matches the left side. So we found another matching route.
So which route is chosen? 0.0.0.0/0, or 192.168.1.0/24? In this case we choose 192.168.1.0/24, because its subnet mask was more specific (has more 1’s) than 0.0.0.0. And when you think about it, this route is valid to reach anything on the 192.168.0.1 network, whereas the 0.0.0.0 path could be used to reach any destination. The route to the network we are on right now (192.168.1.0/24) is more specific and is the route we will choose.
Default Route
Let’s try another example.

Suppose our IP is still 192.168.1.7 and we want to send a packet to 203.0.113.17.
Starting from the bottom again, if we bitwise AND against the netmask, it doesn’t match anything. And, in fact, it doesn’t match a single route except for 0.0.0.0/0. And, if you think about it, for IPs that aren’t nearby on our network (192.168.1.X), they will never match any routes except for 0.0.0.0/0. And because bitwise AND against 0.0.0.0 always results in 0.0.0.0 and matches the left side – 0.0.0.0 – this route will always match no matter what the destination is.
0.0.0.0/0 is known as the default route. It is called that because… well, it is the default. When we don’t have a more specific place to send a packet, we can still send it on the default route.
What would happen if there wasn’t a default route? Well, in that case, there often wouldn’t be a matching route, in which case the packets just get dropped – they never get sent.
This would also make the internet not work. This is because the default route almost always points towards the internet, or more specifically, towards your router which is connected to the internet. Every time your computer tries sending a packet to an internet destination, that IP isn’t going to exist on your local network. So your computer will consult its routing table, find the default route, and send it on its way. So if you didn’t have a default route, you wouldn’t be able to reach anything on the internet.
Gateways, Interfaces, and Hops
We just went over how your computer looks up routes in the routing table. I said it was like looking up somebody’s number in a phone book. In that analogy, you then take that phone number, dial it in so good into your rotary telephone, and then through the magic of telephones you are connected to them.
When your computer finds a matching route in the routing table, what information is listed there and how does it get the packets where they need to go? As I mentioned, there are two things found there: the gateway (or next hop) and the interface.
The interface is basically just an ethernet port. It is the device through which the packet must pass through to exit your computer and move onward to its intended destination. In the routing table on windows it is labeled with an IP address, and that is the IP address corresponding to that specific interface. If you are like most people and only have one network interface on your computer active – either an ethernet port or a wireless card – then that interface will get an IP address via DHCP and this will all happen automagically.
Or, to make things simpler for you, because I know that skull of yours is pretty thick, point your peepers over here:

This is the output of ipconfig. Note the header there, that says Ethernet adapter Ethernet? That is the interface. If you had a wireless card, then ipconfig would list that as well.
That leaves the gateway, or next hop. The thing to realize about IP routing is that there are a lot of stops along the way for a packet to reach the internet, just like when you are tracking a package in the mail. There are several legs along the journey – hops. But in this case, each hop is a router.
You can actually find the specific set of hops between you and any particular destination using the command tracert <destination IP>, such as tracert 8.8.8.8. This will map out the path between your network and that particular IP. For example, here is the path between me and 8.8.8.8, google’s DNS server:
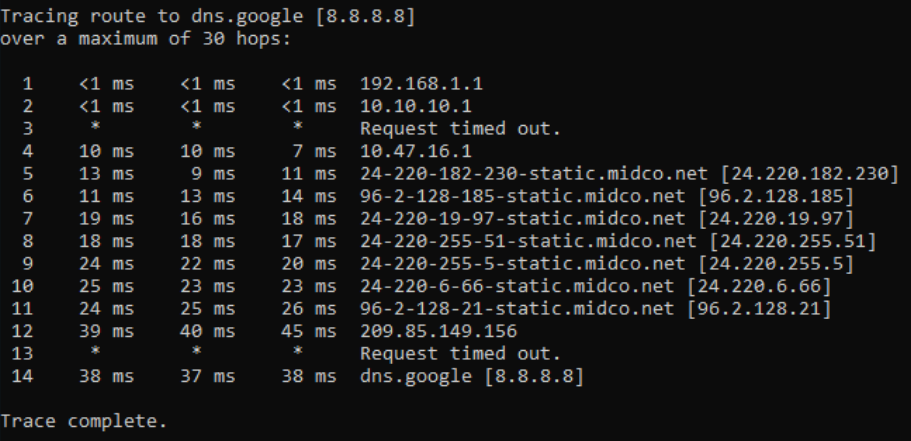
So there are 13 routers between me and google. In this case the majority of them are operated by an ISP, Midco. So every time I do a google search, a bunch of packets from my computer hop their way along this path, and then the return packets from google hop back along the same (or similar) path. When you think about all of those hops, it is remarkable that modern internet connections are as fast as they are.
So when your computer looks through the routing table and finds the best route, it will find the associated gateway. It then sends the IP packet out of that interface, and it is sent to the IP address noted in the gateway field. But there is a slight twist.
Any time your computer sends a packet, the recipient is either on the same network or on a different network. And there is a notable difference between these two cases. Packets sent to a destination within the same network don’t pass through the router at all.
In other words, you don’t actually need a router. Sort of. If all you needed was for computers on your network to talk to each other, no router is required. You would need to set static IPs on them, or have something else running a DHCP server so they get IP addresses, but once they have IP addresses and are physically connected there is no actual need for a router.
Let me remind you again why it is called a router. It routes IP packets. And why is that required? It is required because we want things on different IP networks to talk to each other. So if we don’t care about talking to different IP networks, we don’t need a router at all.
And, for the same reasons, computers on different networks cannot talk to each other without a router in the middle. Routers sit on network boundaries and bridge networks together.
These two cases – same network vs different network destinations – appear differently in the routing table. When the routing table says the gateway is On-link, it means it is on the same network as you, and therefore doesn’t have to go through a router. So your computer can just send the packet directly to the destination computer.
Any time your computer sends a packet that does go to a different network, it must be passed through a router. In these cases, the gateway listed in the routing table is the router the packet gets passed to. This will generally be your router at home.
To reiterate – your computer wants to send a packet, it looks through the routing table. It inspects all the available routes, and from the ones that match it chooses the best route. It then finds the associated gateway and interface. The gateway tells us who on the local network to send the packet to – either the recipient directly, or the router if we are sending packets to a different network. The interface is just the network device – ethernet port, wifi – that the packet gets sent out of.
Oh, and one last thing in this section. Gaze longingly at this picture:

This is the third time I have used this picture, but I know you have short term memory. There are three things listed here: The IP address, subnet mask, and default gateway. We already talked about the first two. What is the default gateway?
Well, the default gateway is simply the gateway listed in the routing table for the default route. It is usually set to point to your home router, because as mentioned before you will not have internet access if you don’t do that. Generally speaking, the majority of your IP packets don’t go to other computers on your network – they go to a different network, often the internet. And your computer has no idea how to reach them, but your router does. So the gateway for the default route is set to point to your router. Thus, when your computer can’t find any route but the default route (which is a fallback, essentially), it gets sent to your router.
Packet and Frame Headers
We talked about packets and frames in part 1 of this series. The basic distinction is, frames are at layer 2 (ethernet/MAC addresses) and packets are at layer 3 (IP addresses).
We also talked about picturing them as boxes, where the packet is essentially stuffed into the frame until it reaches its destination, and then it is unwrapped once it gets there.
I didn’t really explain what the actual contents of frames or packets were, though, and I want to touch on it briefly.
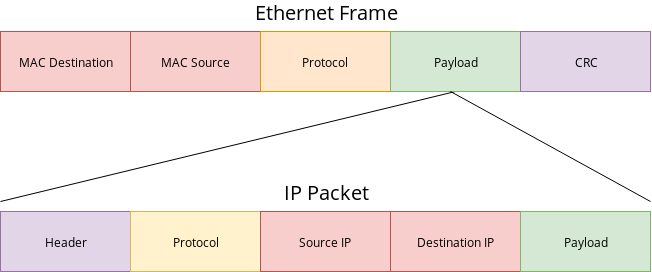
Like I mentioned before, networking is just a bunch of layers. Higher layers are encapsulated in the lower layers. That is a fancy word that just means the higher layers are contained within the lower layers. And this diagram shows us how.
The top row is an ethernet frame. This is the lowest level of data that gets passed around. Much like when you send a letter, it needs a destination address and a return address so that the recipient can send a frame back. And, because all computers on your local network have MAC addresses, that is what they use as addresses for each other.
After the source and destination MAC addresses, we see the protocol field. The protocol field just tells us what higher-level information is encapsulated within this ethernet frame. For example, protocol might be ARP, IPv4, or IPv6. Those are all protocols that can be encapsulated within an ethernet frame.
The payload is whatever has been encapsulated. If the protocol field says IPv4, then the payload is just the actual IPv4 packet. If the protocol field says IPv6, then payload is an IPv6 packet. So protocol tells the receiving computer how it should interpret that payload field.
The second row in the diagram is an IPv4 packet. This IPv4 packet is contained entirely within the ethernet frame in the payload section. The source and destination addresses are IP addresses. The protocol and payload fields work the exact same way. Examples of protocols that are encapsulated within IP packets would be TCP and UDP, which are known as transport protocols (layer 4).
The header and CRC fields aren’t particularly important for this article. The main thing to realize is that IP packets are inside of ethernet frames, and they both use a protocol field to define what the inner packet type is.
Encapsulation is so BOOOORING! Get on with it!
But the capsules, man. Think of the capsules.
Anyway. You may wonder what the point of this information was. The thing I want to focus on in this section is what we fill in for the source and destination MAC and IP addresses.
Let’s say your computer is sending a packet. It finds the route for the packet, and the gateway is on-link. So we know the destination is on our local network and that we don’t need to go through a router. In that case, the source MAC is our MAC address and the destination MAC is the MAC address corresponding to the IP we are sending to (which we can find using ARP). The source IP is our IP address and the destination IP is who we are sending it to.
That is pretty straightforward. Now, what if we were sending a packet to a computer on a different network? In that case, the gateway field will point to our router, which is the first hop on the way to the destination.
Then, the source MAC is our MAC address, but the destination MAC is the MAC address corresponding to the IP of the gateway. The source IP address is our IP, and the destination IP is who we are sending it to.
See the difference? The source and destination IP addresses are the same in both cases, but the destination MAC address differs depending on whether or not the destination is on-link. This has to do with the scope of addresses.
MAC addresses are only used to communicate on the local network. They cannot be used to communicate across a network boundary. IP addresses are the lowest layer that can travel across networks, which is why layer 3 is called the network layer.
What happens when you send a packet to a destination on a different IP network? In that case, as I mentioned, the destination MAC address points to the gateway – your router. Then, when your router sends your IP packet onward to your ISP’s router, the source MAC address is your router, and the destination MAC address is your ISP’s router.
So, conceptually, you have an IP packet, and stuff it in an envelope. You pass that envelope to your router. Your router tears open the envelope and finds your IP packet. It then shoves that into a new envelope, and passes it to your ISP’s router. Your ISP’s router then does the same thing, and it continues up the chain.
So, conceptually, the layer 2 packing information is discarded at every single hop, but the IP information inside is preserved the entire way. Pretty neat, huh? It keeps shedding, like a snake.
Conclusion
You made it to the last section. You read everything and understood it.
Just kidding, that was a trap. I know you didn’t read it all, because you are far too lazy. But look. I included pictures and everything, and it took a while to write, so it should take a while to read. It just be like that, sometimes.
Assuming you did read everything… well, where does that leave us? What did we learn today?
What you learned today is how IP routing works, and how IP packets enable cross-network communication. This, in conjunction with understanding the layer model, is the core foundation for understanding how the rest of networking works. All sorts of things – TCP, DHCP, HTTP – they all build off of these basic layers we covered today. I find a good understanding of these concepts to be very useful when you have to troubleshoot difficult network problems. In particular, I want to stress understanding what happens on layer 2 (ethernet) and layer 3 (IP).
That’s all I got. No more pictures for you. Now get off my lawn and scram.