Note: while this article is about Bitcoin specifically, most of the same principles apply to other cryptocurrencies – they all share a common base.
——————————
By now, you have probably already heard of Bitcoin. Or you live under a rock – but some rocks are nice and shiny, so that is understandable.
If you are like me, you have known of Bitcoin for a while now, but never actually learned much about it. I decided to do something about that, and did some research. Now, I want to share some of what I learned.
The biggest question I had was this: what prevents people from just making their own bitcoins? To me, it seems kind of like online dating. You can lie about anything on the internet. And yet, the system clearly works in practice, somehow.
I eventually learned how it works. And you can too, for only five easy payments of $4.99 a few minutes of your time. But first, some background.
What is Bitcoin?
Bitcoin is a cryptocurrency. Currency, as in that money stuff. Crypto, as in cryptography. You can think of it as a digital currency – the cryptography is just how it is implemented.
Bitcoin can be used in much the same way that normal currencies can be used. For example, you could buy a potato with Bitcoin, provided somebody was selling a potato for Bitcoin. Or, you could exchange Bitcoin for another currency, much like how you can exchange your currency for a foreign currency. The only limitation is what people are willing to exchange. At the moment, Bitcoin is a relatively new and unstable currency, so it is not widely used so far. No potatoes for you.
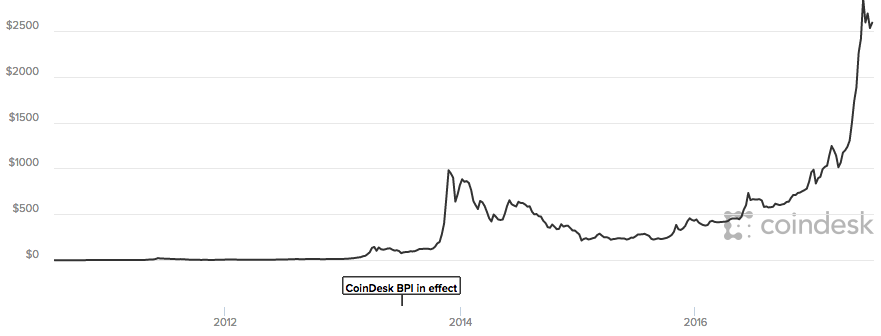
Bitcoin was created back in 2009. It has gradually grown in use over time since then, although it primarily became newsworthy after its exponential growth in value:
At the time of writing, the value of 1 bitcoin is $2533 $2258 $2797. There is a lot of speculation about the future of Bitcoin, and whether or not there is currently a bubble in the market. Very interesting, but not the topic for today.
Being a digital currency, Bitcoin doesn’t have a physical representation, such as physical coins or a paper note. Instead, when you want to do things with bitcoin, you use software commonly called a wallet.
Bitcoin Wallets
Wallets are programs that allow you to send, receive, and store bitcoins. They are, as the name implies, much like physical wallets. You can think of them as a bank account.
Suppose you want to send me some money. We are best friends, after all, and I need the funding to start up my fragrance business. In order to send me money, you need to know where to send it. This is where Bitcoin addresses come into play. Every wallet has one or more addresses. Let’s say this is the address of my wallet:
1BvBMSEYstWetqTFn5Au4m4GFg7xJaNVN2
You simply specify the address and the amount to send, and your wallet will do the work for you. Voila. You have now sent me some money. When I open my wallet, it will now include what you sent me.
Wallets interact with each other over the Bitcoin network much like how computers interact with each other over the Internet. Wallets are only one type of program that interacts with the network. Many different types of devices – desktops, laptops, smartphones, and so on – all use the Internet. Likewise, different kinds of programs use the Bitcoin network, including wallets. These programs interacting with the network are known as nodes.
How do you get bitcoins in the first place? There are three primary ways. First, somebody who has bitcoins can send some to you. Second, you can buy some bitcoins from a coin exchange in return for other currencies, such as USD or even other cryptocurrencies. Third, you can mine bitcoins.
So far we have covered the basics of what Bitcoin is and how you use it. But the question remains: how does any of it actually work?
Wallets and Keys
What the wallet really does for you is store some keys. Not car keys or house keys, but cryptographic keys. These keys are basically very long, very random passwords – kind of like Bitcoin addresses.
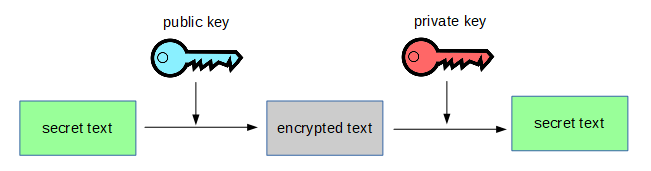
Bitcoin uses something known as public key encryption. In public key encryption, keys are generated in pairs: a public key, which everybody is allowed to have, and a private key, which you keep a secret. These key pairs have a very special property.
When you encrypt something with the public key, it can only be decrypted with the private key, and vice versa. Additionally, you cannot figure out the private key from the public key, or the public key from the private key.
Imagine that I want to send you a secret message. We will say the secret message is “blue poodle,” because why not. You create the pair of keys and give me the public key. I encrypt the message with the public key and get “rh0%u<pwdd5”. I then send the encrypted message to you.
Now, you have a lot of friends (surprisingly). Being such a popular person, everybody else wants to send you secret messages too. So you give out your public key to anybody that asks for it.
Now everybody has the public key, and all the messages are encrypted with the public key. What if somebody reads my secret message?
They cannot, because they don’t have the right key. The secret message was encrypted with the public key. It can only be decrypted with the private key. So nobody else can figure out what the secret is, except the person who has the private key – which is you. Everybody can send you secret messages and only you can read them, like a locked dropbox.
What would happen if you encrypted a message with the private key? In that case, anybody who has the public key – that is, everybody – could decrypt the message.
In other words, the keys undo each other. They are literally made for each other, how romantic. And because you cannot figure out what the opposite key of the pair is when you only have one of them, you can safely give out the public key and keep the private one for yourself.
That’s, uh… interesting, but what does that have to do with Bitcoin?
As I was saying, your wallet stores these key pairs for you. Your Bitcoin address is actually a shortened form of a public key. Much like a public key, you can give it out to anybody. The worst thing that can happen is somebody giving you money.
The private key, on the other hand, must be kept secret. Super-duper, tippy-top secret. Why? Because the private key is how you prove you are the owner of the bitcoins sent to your public address.
It makes sense to use the private key to prove ownership because only the creator knows what it is. Remember, though, that this is the internet: people lie about everything. How can you prove you have the private key without giving away the private key?
Let’s return to our secret-sharing example, and pretend we are in middle school. Everybody likes sharing secrets – especially sharing the secrets of others. Now, suppose one day somebody set up a locked dropbox that anybody can put secret notes into. You want to find a way to know for sure who has access to the box. You ask around, and a lot of people claim they are the one that set it up. How can you know for sure?
One method is to come up with a secret message. Let’s say this time it is “red camel.” Next, you put that message into the box. If somebody can tell you what message was put into the box, they have proved they are the owner because only the owner has access to it.
In the same way, your private key can be used to prove you are the owner of the bitcoins you have. It is like a digital signature that cannot be forged. Only you can create the signature, but it is easy for anybody to verify the signature is yours, using your public key.
You have been rambling on about keys for ages. Are you ever going to get to the point?
Sigh. People have no patience these days.
The point is, your wallet creates and stores pairs of keys. The private keys are kept secret, and the public keys are given out to everybody. Because random strangers giving you money isn’t a problem, anybody can send you money knowing only your public key. However, in order to spend your money, you have to prove it is yours by using your private key to create a signature. In other words, if somebody has your private key, they have your money. Similarly, if you lose your private key – maybe you have a hard drive failure – you also lose access to the money sent to the associated public key, because you can no longer prove ownership.
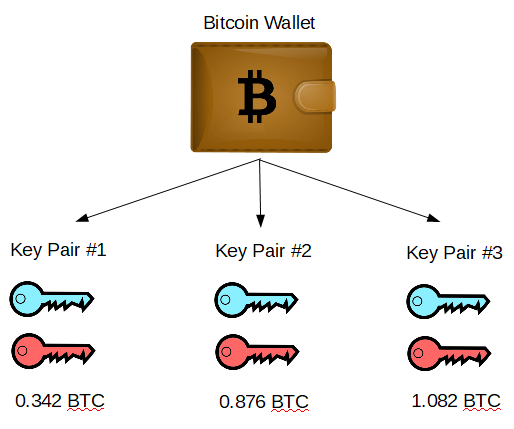
It is important to note that the wallet itself doesn’t store money, it stores keys. Money can be associated with any given pair of keys. The balance of each “account” – that is, each key pair – is simply what was sent to your Bitcoin address (equivalent to your public key) minus what was spent using the private key of that pair.
Your wallet can manage many different pairs of keys. In fact, it is recommended to use a given Bitcoin address to receive a payment only once. Requiring so many key pairs isn’t a problem, because wallets can generate any number of new addresses and associated keys when needed. When you are making a payment, your wallet takes money associated with other sets of keys in your wallet until it accumulates enough. In summary, your wallet manages many pairs of keys (better than you do), and while it behaves as if it is a single account, it is really just coordinating among many sets of keys that are under your control.
The Blockchain
Payments in Bitcoin are known as transactions. Wallets make transactions seem magic, but… how do they actually work? Where are transactions even sent to?
This is where the blockchain comes in. It is the backbone behind the current set of cryptocurrencies, and is the primary innovation of Bitcoin.
The blockchain is a public ledger. It contains a record of every transaction that has ever been made since the beginning of Bitcoin. That is, like, a lot of transactions.
The blockchain is public because it is distributed. Everything that participates in the Bitcoin network, including every wallet, has a copy of the blockchain. The blockchain grows over time as more and more transactions are added to it. Every time a transaction is added, that change to the blockchain is replicated to everything with a copy of the blockchain. How does that work?
Suppose I am having a party at my house tonight. Everybody will come, obviously, but only if they know I am throwing a party. I want to tell everybody about the party so they can come. But it will take a long time to tell everybody (because I am so popular), and I don’t have everybody’s phone number. What I can do is have other people do my work for me. I will tell everybody I am in contact with about the party, and I will instruct them to tell everybody they are in contact with as well. They will also pass on my instructions. In this way, news of the party will spread through everybody everywhere, as each person passes on the message to those nearest them. Eventually, you reach everybody.
The blockchain works the same way. When a wallet creates a transaction, it sends it to every other wallet it knows. And those wallets then send the transaction to every wallet they know, and so on. In this way, the transaction is added onto everybody’s copy of the blockchain.
You may be wondering why it is called the blockchain. The name is actually quite intuitive, because the blockchain literally is a chain of blocks. Of course, this is a meaningless answer if you don’t know what blocks are.
A block is just a collection of transactions. Individual transactions cannot actually be added to the blockchain. Instead, transactions are grouped into blocks, and blocks are added to the blockchain instead.
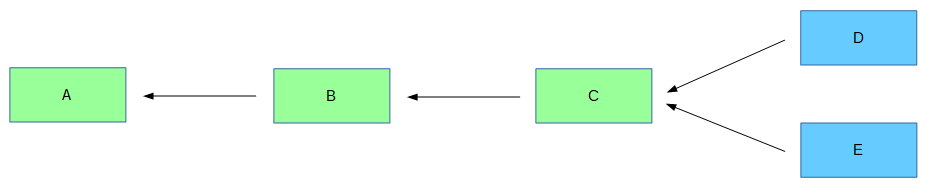
The blockchain consists of many blocks linked (chained) together. Suppose we start with block A. Then, we add block B, and link it to A. We then add a third block, C, and link it to B. The chain looks like this:
Each block points back to the block that happened before it. The blockchain represents a history of transactions over time, where more recent blocks (like C) represent more recent transactions.
If you follow these links backwards in time, you will eventually reach a block that doesn’t link to anything. This block is known as the genesis block, and it is the first block in the chain. Time “begins” there as far as Bitcoin is concerned.
Where do blocks come from?
Well, when one block loves another block… wait, no, not that.
When a transaction is created, it it broadcast on the network. Special nodes called miners collect these transactions into blocks, and then broadcast the blocks on the network, at which point all nodes add the blocks to their respective copies of the blockchain. What miners are and why they make blocks will be explained later.
Using the Blockchain
Because the blockchain records every transaction that has ever happened, we can use it to figure out how many bitcoins everybody had at any given point in time. To do this, we simply start at the genesis block and work our way along the blockchain. If somebody sent you money, your balance is then increased by that much. Likewise, if you make a payment, your balance decreases by the payment amount. By following and reenacting this history, we can determine how many bitcoins anybody has right now.
This basic mechanism is what enables most of the verification in the Bitcoin network to be performed. For example, suppose you have 10 bitcoins, but try to make a payment using 20 bitcoins. When every node receives the transaction from your wallet, they check it for themselves to make sure everything is valid. In this case, they would trace through your history, find out you are not, in fact, the owner of 20 bitcoins, and would not accept your transaction. In other words, the Bitcoin network rejected your attempt at fraud.
That is just one type of verification. Another is verifying that the bitcoins are only spent by their owner. That can be verified using the public and private keys, as we went over before. Other types of verification follow the same basic principle: if you have an accurate history of all transactions, you can determine if a given transaction is valid.
The question at the beginning of the article was this: what prevents people from just making their own bitcoins? The answer, as we saw from this example, is that the rest of the network would not allow you to do it because it does not match the public record.
We aren’t done yet, though. As it turns out, there is an additional problem the blockchain must solve.
Double-Spending
The double-spending problem is much like it sounds: when you spend the same money more than once.
Double-spending is the equivalent of giving somebody a $5 bill, then giving somebody else the same $5 bill. You cannot do that in real life, because you only have one of that particular $5 bill. However, digital things can be copied, and there is no clear way to prevent copies – just ask the movie industry.
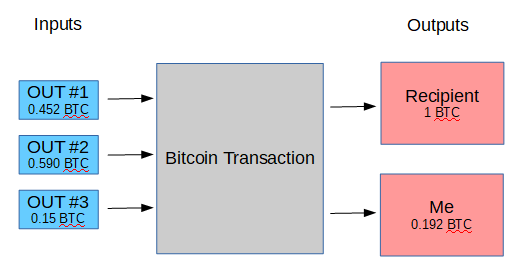
Bitcoin has a solution for this. When a transaction is created, it must list input and output sources. Input sources are where the money comes from. Output sources are where the inputs go – like to the Bitcoin address you are sending money to.
When you create a transaction, the input sources must be previous transactions outputs sent to you. Once a previous transaction output is referenced in this manner, it can never be used again. No money is lost, however – if the sum total of the inputs is more than you want to pay, you simply have two outputs: one to the recipient, and one back to one of your Bitcoin addresses. A future transaction can then reference the latter output where you paid yourself.
Explicitly referencing where money comes from enables the Bitcoin network to detect the most primitive kind of double-spending. When a node receives a new transaction, it looks back at the blockchain history to make sure none of the inputs were spent before. If they were spent before, the transaction is rejected.
There are other types of double-spend attacks that are more complex. Most of them have to do with timing tricks.
Remember earlier when we talked about how the blockchain is replicated across the network? The blockchain does replicate that way, but not instantly. Different parts of the network have slightly different copies of the blockchain at any given time, before the changes have propagated. For any given transaction, some nodes receive it before others.
Suppose I am trying to double-spend. I am going to buy something from a merchant that, once sold, is irreversible – a digital code, for example. The goal in this kind of double-spend attack is to trigger the irreversible action, but then invalidate the transaction so you get your money back. The key is to figure out how to invalidate the transaction.
In order to pull this off, I create two transactions. One is a valid payment to the merchant. The other is a fraudulent payment that uses the same coins – the same outputs from prior transactions – but sends them back to me instead.
Because these two transactions both spend the same coins, they cannot both occur – they are mutually exclusive. For a given node, whichever one is received first will be valid, and the one received after will be rejected because those coins have already been spent.
And, obviously, if I pay myself a given amount, I have the exact same amount of money as I did before. The fraudulent transaction is basically equivalent to saying “nothing happened.” But it is important that it spends the same coins as the other transaction, otherwise it would just be two valid transactions that would both be accepted.
Once I have created the transactions, I send the valid transaction to the merchant, and broadcast the fraudulent transaction to the Bitcoin network. The merchant sees the valid payment, and gives me my digital code. Now, both of these transactions are spreading throughout the network, reaching more and more nodes over time.
It is a race. This race occurs for each individual node on the network. Whatever transaction reaches a given node first “wins.”
Eventually, one of the transactions will be included in a block before the other, and enter the public record.
If the fraudulent transaction ends up in the blockchain, the publicly accepted record is that I paid myself – nothing happened. The merchant did not receive a payment. But I still have the digital code. I have successfully conducted a double-spend attack.
Fortunately, Bitcoin prevents this kind of attack by providing a way to wait for the network to achieve consensus. In this specific case, the merchant could wait to see which transaction wins before giving out the digital code.
The Purpose of Blocks
Blocks are actually the solution to the double-spending problem. The primary purpose of blocks is to “confirm” history, so that people can be reasonably certain that transactions made in the past can never be reversed.
Double-spending is a class of problems that threaten the integrity of this shared history, but not the only one. For example, the Bitcoin network’s consensus works on the basis of the shared blockchain. But how do new nodes get the current blockchain in the first place? They only know what other nodes tell them. What if other nodes give them a fake copy of the blockchain?
As you can see, there are a number of things to be concerned about. But in order for the system to work, there needs to be a method for all the nodes to agree on the correct history. If the nodes disagree, nothing would work. It would be like if one day your bank just decided you had no money.
Blocks and the blockchain are designed to ensure the network agrees on what transactions are valid. All transactions must be in a block. This means that nodes never disagree about individual transactions, but rather an entire block of transactions. Blocks have an additional property: all transactions contained within a block are considered to have happened at the same time. It is like if a bank only updated account balances at the end of the day, and that in order to reverse a transaction, it would have to reverse every transaction that occurred on that day.
New blocks that are created are shared throughout the network, and each node adds it to their copy of the blockchain, assuming it is valid. Every node checks the block to make sure it is correct, so blocks containing invalid transactions are not added to the blockchain.
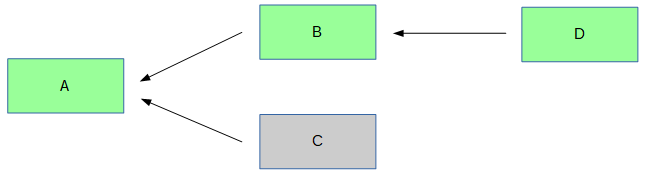
For various reasons, there can be multiple alternative histories. This is often related to timing. For example, suppose two blocks are created at the same time. Which one will become the public record? Such disputes aren’t instantly solved. Instead, we are left with a fork, where there are multiple possible paths in the blockchain.
In this case, multiple blocks link back to the same “parent” block. If you tried following the chain from the start block A, it is unclear if you would choose D or E at the fork. But for the network to work well, we need a single path, which represents a single history.
To solve forks, and ensure the network does agree on everything, all nodes must follow a simple rule: always follow the longest chain of blocks. If a node ever receive a block or chain of blocks that is longer than the copy of the blockchain it has, it discards everything and adopts the longer chain. That way, the longer chain is “right” and will propagate throughout the network.
For example, let’s say a fork has occurred. Everybody agrees that block A came first, but some say block B came second, and others say block C came second. Nodes in the first group will build new blocks starting from block B, and nodes from the second group will build from block C.
Now, suppose that the first group happens to create a new block, block D, before the second group does. The chain then looks like A <– B <– D. The D block is then sent to everybody in the network. Nodes in the second group were working off of the chain A <– C. Because the other chain is longer, they switch to it. Everybody has now “agreed” that A <– B <– D is the correct form of history.
What happens to block C? It is known as an orphaned block. Because it is no longer considered part of history, it is discarded.
Alternative History Attack
The longest chain rule ensures the network converges on a consistent blockchain, but certain attacks against the blockchain are still possible.
Suppose I wanted to double-spend. I could make a valid transaction, and send it to the network. It would be included into a block, added to the blockchain, and the merchant would see the payment and give me the digital code.
But I was clever. Before I sent the transaction, I made a bunch of blocks in secret – an alternative history. I didn’t share them with the network, because I wanted to make a longer chain of blocks.
Now that the transaction has been accepted, I tell the rest of the network about the blocks I made. Because the chain I made is longer, it wipes out the alternative chain – including the block that had the original transaction that paid the merchant.
Sounds like a problem.
You are quite right, it is a problem. The fix, in this case, is to make it more difficult to create blocks.
Bitcoin Mining
You have likely heard of Bitcoin mining. Because some people make money from Bitcoin mining, it has garnered a lot of attention. Mining exists to secure the Bitcoin network. It does this by making history hard to change, so people can be more confident that transactions they have received will not be reverted.
In order to prevent the alternative history attack described above, blocks must be harder to make. Because blocks are just lists of transactions, they can be generated very quickly. To make the task harder, a puzzle was introduced. This puzzle must be solved in order to generate (mine) a block. Because mining a block involves solving a puzzle, the terms “mined” and “solved” are used interchangeably.
The puzzle has to do with hashing. Hashing is like getting a fingerprint of some data, like a file. As an example, suppose we run a hash algorithm, ABC, on the text “bacon.”
ABC is a hash algorithm I came up with just now. Each letter is associated with a number – A=1, D=4, Z=26. To compute the hash, just find the respective numbers and add them. Thus, we get:
2 + 1 + 3 + 15 + 14 = 35
If we ran an actual hash algorithm on that text – let’s say we use SHA256 – we get:
9cca0703342e24806a9f64e08c053dca7f2cd90f10529af8ea872afb0a0c77d4
An important trait of hash algorithms is that changing the input even a tiny bit completely changes the result – take it from the hash of “baconz”:
61ef74d5437b3412e1ad130b1702ba9036a3d872a7492b4f46d33de6397b28c8
The other main trait of hash functions is that they are one-way. Running a hash function on data is easy, but trying to figure out what the original data was given only the hash is extremely difficult. The usual method of reversing this one-way process is brute force – literally trying every possible input until you get the right output. For example, if I was trying to get the hash above, I might try hashing “aaa”, then “aab”, “aac”, and so on until I found the solution. This is also the method usually used to crack passwords.
So what’s the puzzle? Once a Bitcoin miner has created a block, they run it through a hash function. The output of the hash function must be lower than a special number in order to be accepted as valid, which effectively means it must start with a certain number of 0’s. For example, here is the hash of a block:
00000000000000000144fd5b6ebba625238111d44fc2fb876ad1f90df3424fe5
Hash functions are deterministic. When given the same input, they give the same output. To solve the puzzle, miners have to try hashing the block over and over again, with a slight change every time. The slight change is a random number, called a nonce. Every time a miner doesn’t solve the puzzle, they try it again with the next number.
Eventually, the miner wins the “lottery” and gets a random number that works. The puzzle is solved, and the block can be added to the blockchain. Bitcoin mining is just the process of solving the puzzle. This method of securing the network is known as proof of work, because to create a block you have to give the solution for it, and it is difficult to find the solution. This aspect is important, because the proof is easy to verify, but hard to create.
Miners – people running nodes that perform mining – get paid from mining through two means. First, they receive the block reward. This is how coins are introduced in the Bitcoin economy. The first transaction listed in a block is special, and is known as the coinbase transaction. The coinbase transaction gives a miner their reward. The miner specifies the bitcoin address for the reward to be sent to. The money doesn’t really come from anywhere – it is created at that moment from nothing. However, the amount of the block reward is calculated by a special formula, and because every node on the network validates that the block reward is equal to what the special formula says, no miner can take more than the reward allowed for them.
The second way miners get paid is through transaction fees. Each transaction has a fee attached to it. This fee is like a bid from the person sending the transaction. When a miner mines a block, they get all the transaction fees from the transactions in that block. The fee is decided by the sender. Miners simply choose higher-fee transactions first for placement into blocks. It is like a priority system. The coinbase transaction includes both the block reward and the transaction fees.
It is worth noting that miners don’t get paid for doing useful computation. In fact, a lot of effort is wasted in proof of work. Mining blocks is like a race – if you aren’t first, you may as well be last. Because nodes choose the longest chain of blocks, if a miner kept working on the same block after another miner solved a block, they would just fall behind. Instead, when any miner on the network solves a block, every other miner discards the block they were working on. All the work that was done in solving the puzzle is wasted. Effort is often wasted even for solved blocks, because they may end up being orphan blocks.
And even for miners that do solve the puzzle, they haven’t done useful computations. The blocks are hard to compute for the sole purpose of being hard to compute – they are arbitrarily hard. In fact, the difficult of mining blocks changes over time, depending on how long it takes to solve a block. The average block is solved every ten minutes. The network automatically adjusts the difficult of mining to make that time stay the same, even as hardware improves over time. The difficulty is increased by making the puzzle solution need to start with even more 0’s.
Mining and Security
The primary purpose of mining is to secure the network. The rewards for mining simply exist as financial incentives to mine. The actual purpose mining provides is securing the network against the types of attacks outlined earlier.
Why does mining secure the network? Remember, the problem we had before was that blocks were too easy to make, so we didn’t know if we could trust the history other people told us. By making blocks harder to create, we can be more certain the network is secure. But why?
Key to why this secures the network is how the chain part of the blockchain is implemented. Each block contains the hash of the previous block – that is what links them together. Including the hash of the previous block gives the blockchain an important property:
Any time you change a block in the blockchain, you have to re-mine every block that comes after it.
Let’s say I try to change history, and change a block that was added to the blockchain a while ago. If I change anything in the block, the hash of it changes completely. I would need to re-mine it to make it valid again. This would take a while, but I could do it eventually.
However, the block that follows it contains the old hash. It is now no longer valid, because no block exists with that hash now. In order to make it valid, I would need to change its “previous block hash” value. But then I would need to re-mine that block as well. This effect cascades until you reach the end of the chain.
This is equally true if you make completely new blocks. It takes just as long to make new blocks as to modify old ones, because the mining process takes the majority of the time and must be done in both cases.
The blockchain is like a stack of plates. Removing the top plate in a stack is easy. Removing a plate under a few other plates is more difficult, and requires moving every plate on top of it first. Removing the bottom plate is the most difficult, and requires moving every other plate.
In case that analogy was too hard for you, a block is like a single plate.
Why is it important that it is difficult to change the blockchain? Because the blockchain is the authoritative record for who-has-what. If you can change the blockchain, you have a significant power to alter history and conduct the types of attacks outlined above.
However, due to the hash puzzle and linking blocks together, creating blocks is hard, and creating a chain of blocks is even harder. The Bitcoin network makes use of this property by using the concept of block confirmations.
Confirming Blocks
How long does it take for a transaction to “go through”? The most accurate answer is “it depends.” Technically, your transaction reaches most nodes on the network in a matter of seconds. However, it takes a bit longer for it to be included in a block that is successfully mined. At that point, the remainder of the time is decided by the recipient. It could be instantly, an hour from now, or even a day.
In order to understand this, you need to think about transactions a bit differently. When you make a transaction in the Bitcoin network, you are just adding an entry to the public ledger. Other nodes on the network calculate your “net worth” by following the chain of transactions you have made. However, they may delay counting recent transactions for a period of time, to make sure they will not be reversed by blockchain attacks.
The introduction of hash puzzles and linking blocks together serves to make it harder to conduct double-spend attacks, but not impossible. While the average time taken to solve a block is ten minutes, the time to solve any given block can range considerably, since the solution is random. A block could be solved in a minute, or it could take an hour. However, the time taken to solve a block follows a particular distribution, so times around ten minutes are most likely. It is much like saying people can be 4ft or 7ft tall, but most people are around the middle of that range.
Suppose a merchant accepted a transaction as valid once it was included in a block. If somebody manages to generate two other blocks before the rest of the network generates another block, they can conduct an alternative history attack still. The security of the hash puzzle is probabilistic in nature.
Let’s say I am mining on a bunch of computers, and have 10% of the network hash rate. Hash rates are how many times a miner attempts to solve a block per second. The network hash rate is just the sum total of every miner’s hash rate. Thus, the network hash rate is effectively the “power” of the network. If I have 10% of the hash rate, I have 10% of the power.
What is the probability of me mining 2 blocks before the rest of the network? The answer involves statistics and that math stuff, and I don’t understand it myself. The probability is 21%, and it gets lower and lower if more blocks are needed.
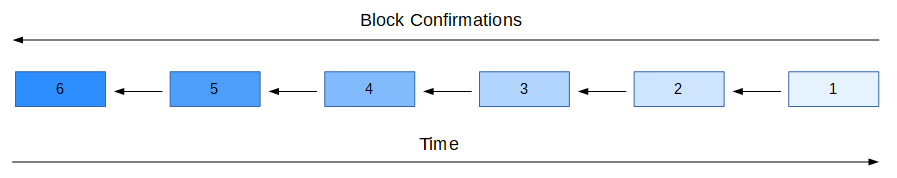
To minimize the risk of a transaction being reversed, standard bitcoin wallets and merchant usually wait for a given transaction to be confirmed a certain number of times. A confirmation is when a transaction is included in a block, or when another block is added onto that block. For example, a transaction that hasn’t yet been included in a block has 0 confirmations. Once it has been included in a block, it has 1. When other miners on the network receive that block, they will treat it as part of the chain and build new blocks from it. Once such a new block is added – when the original block gets “deeper” – it now has 2 confirmations.
How many confirmations are needed? It is up to the merchant or recipient, based on how much confidence they want. 6 confirmations is fairly standard. In order for somebody to attack history that is 6 blocks deep, they would need an alternative chain of blocks that is 7 blocks long. In the previous example where I control 10% of the network, the probability of this is .02%. Not impossible, but close enough for comfort.
The basic idea is just to wait long enough. The further back in the chain a block gets, the harder it is to reverse. There is, however, 1 exception. If somebody controlled 51% of the network hash rate – over half of the hardware mining resources – they can successfully attack any length of blockchain history.
Let’s look at the math. If I control 51% of the network, the odds of me solving a block is higher than the rest (49%) of the network. If we looked at the last 1000 blocks mined, we would expect me to have mined roughly 510 of them, and the rest of the network would have mined 490. Thus, if I had kept my 510 blocks secret that entire time, I could replace the existing 490-block chain with mine, erasing that history.
So the Bitcoin network is not secure if anybody or anything (say, an organization or mining pool) has 51% of the network hash rate. Fortunately, such a thing would be incredibly difficult to obtain, and extremely expensive as well. Additionally, there is some financial incentive to not do it.
The incentive is stability. The value of Bitcoin, as with any currency, is heavily influenced by how stable it is. If it is known or suspected that somebody has or could conduct a 51% attack, trust in Bitcoin would fall, and a mass sell-out would occur. As such, even if you could conduct double-spend attacks, you would cause a crash, leaving you in control of something people would quickly abandon.
And if even that isn’t enough, there is also opportunity cost to consider. It would be more profitable to mine bitcoins than attack the network.
Summary
The original question was this: what prevents people from just making their own bitcoins, or lying about what they have?
The answer is that all bitcoin nodes check all transactions against the blockchain. Every transaction references back to previous transactions that are considered valid. Once a transaction is considered valid, it too can be used as a reference for a later transaction. Coins cannot be created from nothing, because there would be no record in the blockchain about those coins.
Bitcoin and other cryptocurrencies are built on cryptographic principles. The security of these systems relies on the integrity of the underlying encryption. Cryptography enables us to do things that don’t initially seem possible, like prove that we are who we say we are, even to random strangers on the internet.
The key innovation in these cryptocurrencies is the blockchain. The blockchain is somewhat complex, but at the end of the day it serves a simple purpose. The purpose of the blockchain is to provide a shared history that is consistent throughout the network, so everybody agrees and the system can function properly.